Add an LDAP Connector Device
Before you are able to import an LDAP group, you must first create a means for Vbrick Rev to communicate with Active Directory and LDAP groups. This is accomplished by creating an LDAP Connector and then running that connector on a host or through a direct connection if you have an on-premise installation. Be aware that the connector will always need to be running on the host you choose for importing and synchronizing your LDAP groups and users if you do not have a direct connection enabled.
Note: Depending upon the Directory Type you choose, most fields are completed for you when adding an LDAP Connector. If you intend to modify those fields and are unsure of exact values, consult the Directory Type’s documentation for more information: |
1. Navigate to the Admin > Devices > Source Devices and LDAP Connectors option.
2. Click Add a Device > Add an LDAP Connector.
3. Complete each section of the form as described below.
Add the LDAP Connector as a Direct Connection
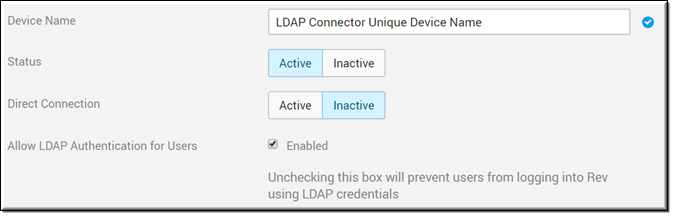
The Device Name section first needs to be completed as either a Direct Connection (normally for on-premise installations) or for use with the LDAP Connector for Rev Cloud that you previously downloaded and installed. In this case, you will need to inactivate Direct Connection and enter at least one Mac Address (of the laptop/server of the previously installed connector).
This example has Direct Connection in inactive status since Rev Cloud is in use.
Field Name | Required | Description |
|---|---|---|
Device Name | Yes | The unique Device Name you will use to import your LDAP groups. |
Status | Designates whether or not your connector is currently active or inactive. | |
Direct Connection | Enabled by default. This setting is used for On-Premise Rev installations to provide a direct connection to Active Directory. If this setting is enabled, you will not be required to download and install the Rev Cloud LDAP connector. You will, however, be required to enter at least one Mac Address which is used to run one or more LDAP Connectors. | |
Allow LDAP Authentication for Users | Enabled by default. Specifies if users will use LDAP authentication. If disabled, user/group sync will use LDAP while user authentication will use SAML. See: Disable LDAP Authentication for Users. |
Add a MAC Address for the LDAP Connector
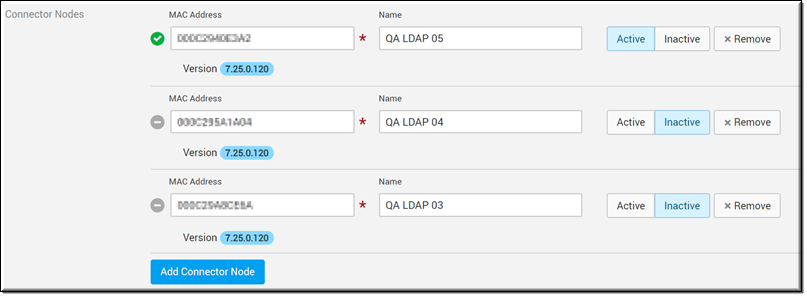
To use the LDAP Connector for Rev Cloud, make sure you disable the Direct Connection and enter a MAC Address for each Connector Node you plan to use. You may configure the status per node or through the entire LDAP Connector as desired (unless there are no active nodes). If more than one node is configured, the system will distribute tasks among the available nodes.
Field Name | Required | Description |
|---|---|---|
Connector Nodes / MAC Address | Yes | Only visible if Direct Connection is set to inactive status. The Mac Address for the Connector Node is required if Direct Connection is inactive and you will be unable to create the connector without it if you plan to run your connector on a host. This should be the address of the host you plan to run your connector from or previously entered connector host location. This is easily obtained by entering the command getmac from a command prompt. The Mac Address is the first line with no dashes. You may add additional nodes by clicking the Add Connector Node button. Further, you may change the status of each node at will by clicking the Active and Inactive buttons. Click the Remove button to remove a node. Note: The LDAP Connector for Rev Cloud version in use is displayed under each address. It is not recommended that different versions of the connector be in use at the same time. The first two MAC Addresses of each node you add may be viewed on the main Source Devices and LDAP page under the Network Address column. |
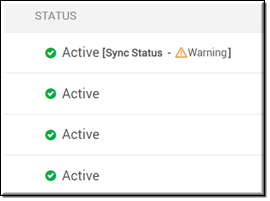
LDAP Connector Status depends on the following node states:
●If LDAP Connector is active and all active LDAP nodes are online: Active
●If LDAP Connector is active and at least one active LDAP node is offline: Warning <# of offline nodes/# of active LDAP nodes>
●If LDAP Connector is active and all active LDAP nodes are offline: Offline (See image above)
●If LDAP Connector is inactive: Inactive
LDAP Server Settings
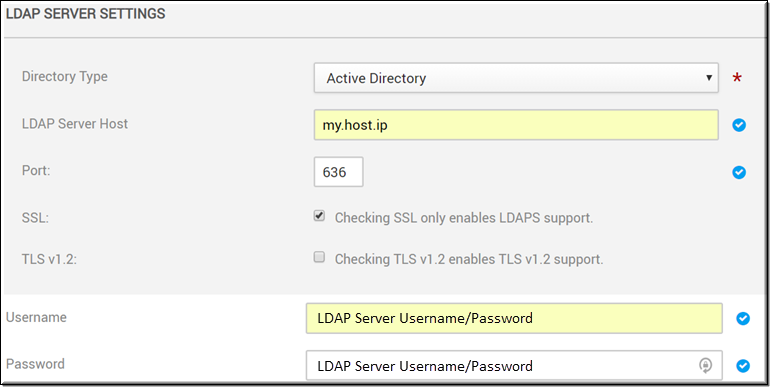
Once you decide how you are going to run the connector, complete the LDAP Server Settings section.
Field Name | Required | Description |
|---|---|---|
Directory Type | Yes | The directory type that the LDAP Connector supports; Note that when you choose a directory type, the LDAP Server Mapping fields will be automatically populated with the recommended default settings for that type. |
LDAP Server Host | Yes | The IP address or name of the host. |
Port | Yes | The default port is 389. Use 636 if using SSL. |
SSL | Indicates the LDAP connection is over SSL if selected. | |
TLS v1.2 | Enables TLS v1.2 support. Must have SSL enabled first before this becomes available. | |
Username | Yes | The user name/password to connect to LDAP Server. |
Password | Yes | The user name/password to connect to LDAP Server. |
Tip: This topic uses Active Directory as the Directory Type when creating an LDAP Connector. However, selecting Generic LDAP is much the same process. |
LDAP Server Mapping
Most of the LDAP Server Mapping section is populated with recommended default values and formats when you choose a Directory Type in the LDAP Server Settings section. The image below displays the server mappings for Active Directory. These fields may be modified if needed. Most fields are required.
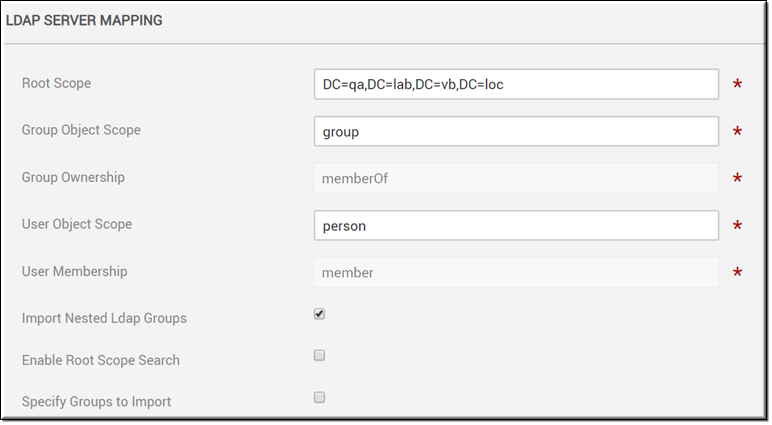
Note: Keep in mind that if you change the Root Scope field in the LDAP Server Mapping section after you have already imported groups and users, you will need to re-import your group. |
LDAP Groups Specification
The LDAP Groups Specification section is used to import specific LDAP groups only and is only visible if the Specify Groups to Import checkbox is selected in the previous LDAP Server Mapping section.
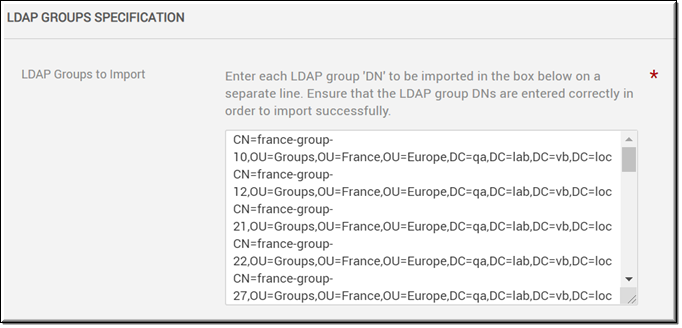
If you are an organization with hundreds or even thousands of LDAP groups, this may take a considerable amount of time to import. You may use the Specify Groups to Import checkbox to enter the LDAP group you want to import instead. This will open the LDAP Groups Specification section where you may enter the Distinguished Name (DN) of the LDAP group to be imported seen in the example below.
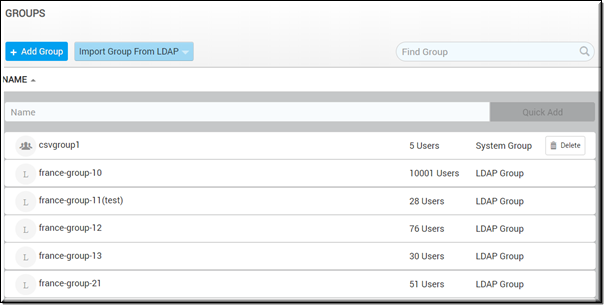
By default, the Specify Groups to Import checkbox is deselected which means that all LDAP groups associated with your Active Directory server will need to be retrieved and displayed for potential import when you click the Add Groups action for an LDAP Connector device or the Import Group From LDAP button from the Groups module, seen in the image below.
Keep in mind:
●You must enter the LDAP DN name exactly as it appears. If it is misspelled or entered incorrectly it will not import. Note: It is not case sensitive.
●If you use this method, you may no longer use the Add Groups action for an LDAP Connector device or the Import Group From LDAP button from the Groups module until the Specify Groups to Import checkbox is once again deselected.
●If the checkbox is deselected and you want to import new groups, then the Reset Connector Sync button must used to manually sync the connector; or you may also wait until the next scheduled sync interval has been performed. See: LDAP Server Synchronization Settings.
User Record Mapping
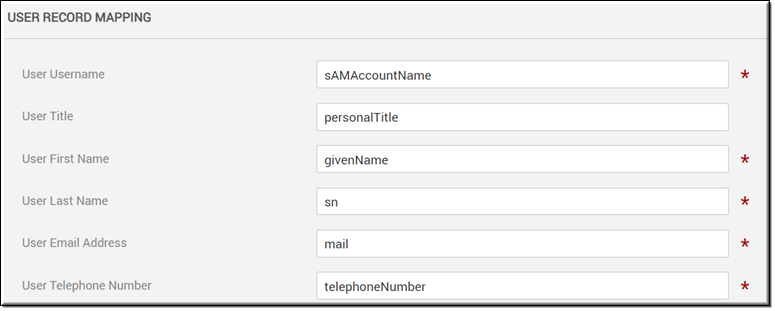
Similar to the LDAP Server Mapping section, the User Record Mapping section is populated with recommended default values and formats when you choose a Directory Type in the LDAP Server Settings section. The image below displays the user record mappings for Active Directory. These fields may be modified if needed. Most fields are required.
Merge Users
The Merge LDAP and non-LDAP users checkbox is disabled by default. If this is checked/enabled, the LDAP connector will process and merge the incoming user even if the user currently exists in Rev (if unchecked, a “duplicate user” error is generated).
Keep in mind:
●The incoming user will be treated as an update and this is permanent and not reversible.
●The update only occurs if both username and email address match.
●The source of the user account will be modified to LDAP.
●If the Rev user account had additional roles, those will be retained.
●If the Rev user account was manually suspended, that user will remain suspended.
●Active and unlicensed status will remain unchanged.
●LDAP fields override Rev user field values, including any blank fields.
●As noted, if this checkbox remains disabled, then the LDAP connector will continue to display an error message for any duplicate username/email addresses found.
LDAP Server Synchronization Settings
The LDAP Server Synchronization Settings section is used to specify the sync interval from Active Directory to Vbrick Rev. You can also specify if Suspended user accounts should be deleted when a sync occurs.
Sync intervals are specified in minutes or hours. The recommended interval is 24 hours; particularly if importing and/or syncing large groups of users so you do not tie up server resources during peak usage time by your end users. Note that you must specify a synchronization interval.
Select the Delete Suspended Users Who have never logged in checkbox to delete those LDAP accounts that were synced and imported but then subsequently never logged in to Rev. An example of this may include a user account that was created and imported but then left the company before logging in.
If your sync needs to be reset for any reason, you may use the Reset Connector Sync link in the Actions drop-down on the All Devices form to do so.